Beware the masters of ‘dark art’ and don’t underestimate cybercriminals – the malware attack that circled the world last month has prompted calls for software updates and a tightening of IT security, as experts say that it can and will happen again . . .
It was called WannaCry for a good reason and probably more than a few tears were shed – of despair as well as fury – as the latest malware attack became an epidemic, stripping data and locking down computer systems around the world.
We shouldn’t be surprised. Interpol reports that the fastest-growing crime, globally, is cybercrime. In the aftermath of the WannaCry ransomware attack of May 12, the international police organisation’s secretary general, Jürgen Stock, said specialists from its 190-member countries were examining the after-effects while preparing for further threats.
Stock described the investigation into the attack as “complex and globally significant”, adding: “It is essential the full scale and scope of it is established if we are to assist member countries, deliver an effective response and put measures in place to prevent future cyber attacks against critical infrastructures.”
But putting it perhaps more scarily succinctly was IT expert and research analyst for Counterpoint, Satyajit Sinha. He warned that this cyber attack “was not the first and definitely not the last”, adding: “Near term, we expect attacks to target smartphones as well as PCs and IoT devices.”
This particular malware locks an infected computer system and demands a $300 ransom in ‘Bitcoin’ to restore access to files – or face deletion of data. One UK-based IT worker is known to have paid around £70,000 to recover his personal data – there may well be others who have reacted similarly. It’s the newest form of extortion.
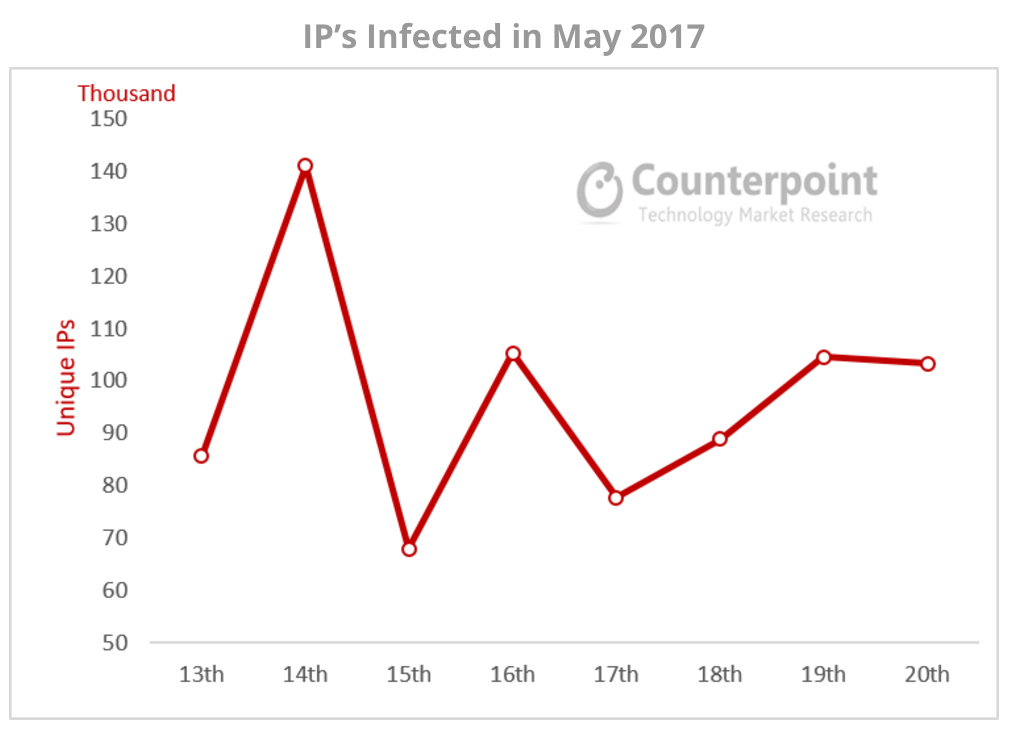
In the first seven days, the WannaCry malware infected more than 130,000 organisations across 150 countries. They included energy companies such as WBSEDC in India, Iberdrola in Spain, Petrobras in Brazil; telecoms – Telefonica, Portugal Telecom, MegaFon and Telenor Hungary; and banks such as Sberbank, Bank of China and Russia Central Bank. And, within two days of the malware crisis, at least 16 hospitals in the UK were forced to divert emergency patients as core equipment was compromised.
The US Department of Defense has said that this year it is updating 4 million computers to Windows 10 – the Pentagon was still using Windows 95 and 98 on several missile control computers. The malware attack – known to target major organisations that are still running software that is out of date – has prompted the DoD to prioritise the move.
Cybercriminals: can you outsmart masters of the dark art?
While the rise of the internet has been a boon for consumers and businesses, it has also opened up this whole new level of criminal activity. A new research report says ever-increasing online connectivity will lead to data breaches that will cost businesses a total of $8trillion over the next five years.
What can we do?
The scenario will be compounded by inadequate enterprise-wide security: big brands and other organisations become vulnerable as old and new IT systems are integrated by tech teams that might have taken their eye off their overall network security, albeit briefly. In other words, computer hackers are swift to spot an unlocked ‘back door’ while the IT guys are busy updating the front door. It’s what hackers are good at – they are highly trained, hugely professional and well funded in their dark art.
If only they were honest . . .
The research, The Future of Cybercrime & Security: Enterprise Threats & Mitigation 2017-2022, forecasts that the number of personal data records stolen by cybercriminals will reach 2.8 billion this year, almost doubling to 5 billion in 2020, in spite of the development of innovative cyber security solutions.
Researchers at Juniper found that SMEs (small and medium enterprises) are especially at risk from cyber attacks, spending less than $4,000 on cyber security measures this year. Only marginal increases in security spend are expected over the next five years. These firms also tend to run older software, which have been exploited by the WannaCry malware and others.
The research points to a need for companies to put more resources into cyber security and system upkeep – treating them as a vital element of workplace safety.
The author of the research, James Moar, said: “The attacks on hospital infrastructure show that inadequate cyber security can now cost lives as well as money. Businesses of all sizes need to find the time and budget to upgrade and secure their systems, or lose the ability to perform their jobs safely, or at all.”
Cyber security expert Giridhara Raam told The GMA that effective data back-up is vital to ensure files are not stripped in a malware attack. He said: “Once ransomware has encrypted your files, there’s little you can do. Having a back-up of your files is the only sure way to restore them. If the ransomware is weak, it can sometimes be hacked to recover the data. But that’s not going to work on a well designed, professional ransomware attack like WannaCry.
Read also:
Under cyber attack: ‘Hello, I’m WannaCry – pay me to decrypt your files’
Web analytics and safeguarding your site in the ‘age of impersonator bots’






Leave your thoughts